Latest Version
7.2.0.54
July 15, 2025
MicroWorld Software Services Pvt. Ltd.
Tools
Android
0
Free
com.eScanAV.certin
Report a Problem
More About eScan CERT-In Bot Removal
Understanding Mobile Bots: Protecting Your Device from Cyber Threats
In today's digital landscape, the threat of mobile bots looms large. These malicious entities can compromise your device, leading to severe privacy breaches and data theft. This article delves into what mobile bots are, how devices become infected, the impacts of botnets, and essential precautions to safeguard your device.
What is a Mobile Bot?
A mobile bot is a type of malware that operates on devices lacking adequate protection, such as antivirus software. Similar to computer bots, mobile bots can infiltrate your device, integrating it into a botnet controlled by hackers. Once infected, your device becomes a tool for various malicious activities, allowing the botnet owner to access sensitive data, applications, and internet usage.
How Do Devices Get Infected?
Infection occurs when unprotected devices encounter various forms of malware, including Trojans, worms, and other malicious software. Common infection vectors include:
- Email Attachments: Malicious links or attachments in emails can introduce malware.
- Deceptive Apps: Downloading seemingly legitimate applications can lead to infection.
- Website Visits: Browsing compromised websites can expose your device to malware.
- Downloads: Files downloaded from untrustworthy sources may contain hidden threats.
Impacts of a Botnet on Your Device
Once a device becomes part of a botnet, the consequences can be dire. The hacker or botnet owner can:
- Steal Data: Access and copy all existing data stored on your device.
- Install Malicious Software: Download harmful applications or payloads without your consent.
- Block Communications: Prevent incoming and outgoing calls and texts.
- Send Unauthorized Messages: Make calls and send texts on your behalf.
- Access User Accounts: Gain entry to sensitive accounts, including banking details.
- Exploit Internet Connection: Use your internet for malicious activities.
- Launch DDoS Attacks: Execute large-scale Distributed Denial of Service attacks.
Precautions to Protect Your Device
To minimize the risk of infection, users should adopt the following precautions:
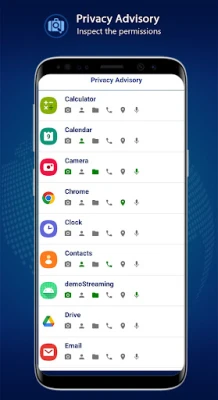
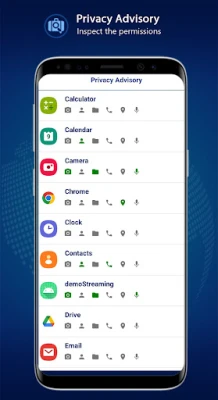
- Review App Permissions: Regularly check the permissions granted to all installed applications.
- Monitor Data Usage: Cross-verify your bills for any unusual data usage, texts, or calls.
- Watch for Battery Drain: Be alert to unexpected battery depletion, which may indicate malware activity.
- Download from Official Sources: Only install apps from reputable app stores.
- Avoid Suspicious Links: Refrain from opening emails or links from unknown or dubious sources.
- Use Antivirus Software: Always browse the internet with a reliable antivirus application installed.
How to Safeguard Your Device from Botnets
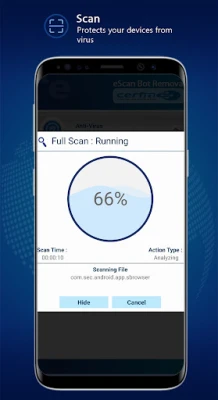
In an era where data privacy is increasingly threatened, protecting your information is paramount. To ensure your device remains secure, consider utilizing the eScan CERT-In Toolkit. This comprehensive tool allows you to scan your device for bots and any ongoing malicious activities. Additionally, it provides insights into app permissions, helping you monitor unusual access.
Features of the eScan CERT-In Bot Removal Toolkit
The eScan CERT-In Bot Removal Toolkit offers a range of features designed to enhance your device's security:
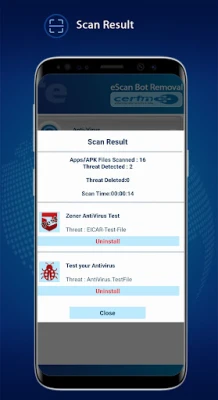
- Comprehensive Detection: Identify and eliminate the latest botnet infections, viruses, spyware, adware, and malware from your smartphone.
- Cloud-Based Virus Signature Database: Benefit from a constantly updated database that enhances detection capabilities.
- Threat Consolidation: View a consolidated display of detected threats, allowing users to select and uninstall malicious applications easily.
- Privacy Advisor: Receive guidance on maintaining your privacy and securing your data.
Conclusion
Understanding mobile bots and their potential impact is crucial in today's interconnected world. By taking proactive measures and utilizing tools like the eScan CERT-In Toolkit, you can protect your device from becoming a part of a botnet. Stay informed, vigilant, and secure your digital life against evolving cyber threats.
Rate the App
User Reviews
Popular Apps










Editor's Choice